Design
Network Ports used for communication
Introduction
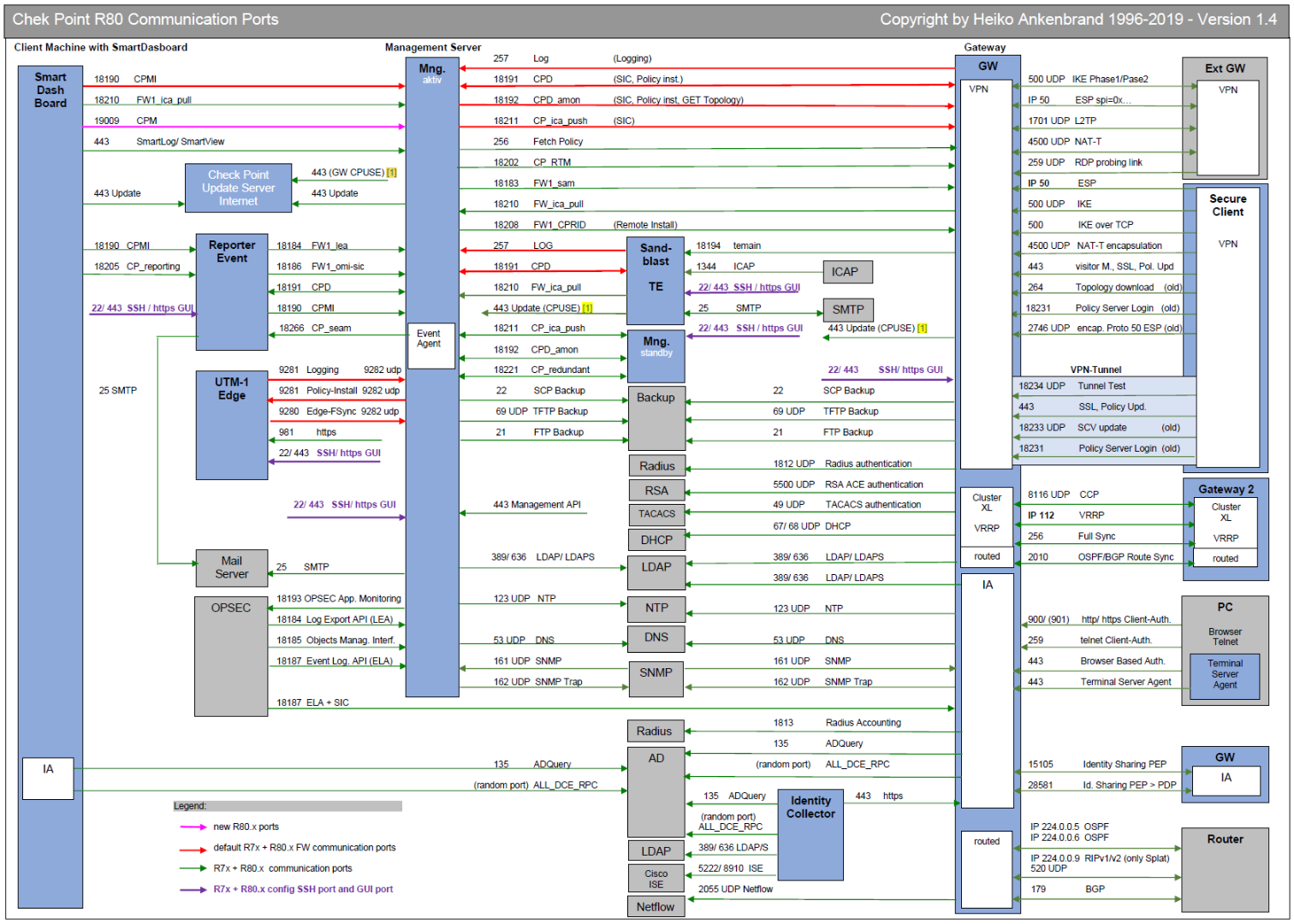
This drawing should give you an overview of the used R80 and R77 ports respectively communication flows. It should give you an overview of how different Check Point modules communicate with each other. Furthermore, services that are used for firewall operation are also considered. These firewall services are also partially mapped as implied rules in the set on the firewall.
Link
Thank you Heiko Ankenbrand for creating such a valuable overview:
Overview
Download
https://www.ankenbrand24.de/wp-content/uploads/2019/12/Ports_1.5a.pdf
Log Files location Check Point
Here are the different Log File locations on a Check Point Appliance:
| Feature | File Location |
|
Alerts |
|
|
Command auditing |
|
|
CPD |
|
|
Distribution |
|
|
Dynamic Routing |
|
|
Expert mode shell auditing |
|
|
FWD |
|
|
FWK |
|
|
Gaia Clish |
|
|
Gaia |
|
|
General |
|
|
SMO |
|
|
Installation |
|
|
Installation - OS |
|
|
Log Servers |
|
|
Policy |
|
|
Reboot logs |
|
|
SGM Configuration Pull Configuration |
|
|
VPND |
|